Cybersecurity tips for small businesses: A 2025 guide to staying safe online

High-profile breaches at large companies make headlines, but small businesses face the same types of attacks every day, just without the resources to recover.
That’s why it’s critical to take proactive steps now, before a single phishing email or weak password puts your entire operation at risk. This guide breaks down essential cybersecurity practices tailored for small businesses: simple, effective, and affordable.
Why cybersecurity matters for small businesses
Most small business owners assume they’re too small to be a target. After all, why would cybercriminals waste time on a company with a handful of employees? The truth is, that assumption is exactly what makes small businesses vulnerable and attractive targets.
The growing threat landscape
In recent years, cybercriminals have shifted their focus toward smaller businesses, knowing that many don’t have the budget or staff to maintain strong defenses.
Ransomware attacks, phishing emails, and data breaches now hit small companies at a growing rate. According to Verizon’s 2025 Data Breach Investigations Report, small-to-medium businesses (SMBs) were targeted nearly four times more than large organizations in their dataset, though that’s also because there are a lot more SMBs out there.
For cybercriminals, small businesses offer a high return with minimal effort: less security, fewer safeguards, and enough valuable data to steal or hold for ransom.
Why small businesses are prime targets
Breaches rarely begin with sophisticated attacks. Most start with routine mistakes: password reuse, phishing clicks, or poor access control. The same Verizon report notes that 60% of the 12,195 confirmed breaches they investigated in 2024 involved the human element, including employee errors, credential misuse, and misconfigurations. This may include employees falling for scams, mishandling credentials, or configuration errors.
For small businesses, ransomware remains one of the biggest threats. According to the same report, 88% of SMB breaches involved ransomware in 2024, compared to 39% for larger companies.
Cost of a cyberattack for small-to-medium businesses
According to Microsoft, which partnered with SMB research firm Bredin to conduct an online survey of 2,000 U.S. and U.K. businesses, the average total cost per breach for an SMB in 2024 was around $254,445, with more severe cases reaching as high as $7 million.
A 2024 study by Vanson Bourne, commissioned by ConnectWise, a company that provides IT management and cybersecurity software for service providers, found that 78% of small and mid-sized businesses believed a successful cyberattack could force them to shut down. While not all attacks lead to closure, the long-term damage, from reputational loss to client attrition, can be just as devastating as the immediate financial hit.
Top 10 cybersecurity tips for small businesses
1. Train employees on cybersecurity awareness
Your employees don’t need to be security experts, but they do need to know and practice good cybersecurity habits. That’s where targeted cybersecurity training makes the difference.
How to implement effective training
- Keep sessions short but frequent. Aim for quarterly refreshers.
- Use real phishing examples. Collect recent scams and show how to prevent them.
- Run phishing simulations. Periodically test employees in controlled scenarios.
- Reward correct reporting. Encourage staff to flag suspicious emails, not hide mistakes.
The goal is to build instincts that make employees pause and verify before acting.
Free resources for small businesses
Small businesses often lack the resources of larger organizations when it comes to cybersecurity, but there are excellent free tools available to help bridge the gap. One great starting point is the Cybersecurity and Infrastructure Security Agency (CISA)’s Cyber Essentials guide that lays out fundamental actions any small business can take to boost its security. It’s designed for non-technical leaders and offers a clear roadmap for establishing a stronger security posture.
Another valuable resource is the Federal Trade Commission (FTC)’s Cybersecurity for Small Business guide. It provides plain-language tips and information on topics like phishing, ransomware, and physical security.
2. Use strong and unique passwords
For attackers, stolen, reused, or weak passwords are still one of the easiest ways in. Encourage your team to use strong, unique passwords for every login, especially for tools like email, cloud storage, and financial services.
Managing all these credentials manually isn’t practical, and writing them down invites risk. Realistically, a password manager is the easiest way to handle passwords securely.
ExpressVPN Keys makes it easy to generate, store, and autofill secure passwords across devices, all while keeping them encrypted and protected. Built into the ExpressVPN app and included with every ExpressVPN subscription, Keys helps your team stay secure without slowing down productivity.
3. Enable multi-factor authentication (MFA)
Even with a password manager, it’s advisable to protect your critical accounts with two-factor authentication (2FA) or MFA, which requires users to verify their identity through an additional factor (like a one-time code, push notification, or biometric scan), typically on another device, before granting access.
For small businesses, this single step can block the vast majority of unauthorized login attempts. According to Microsoft, MFA can prevent 99.9% of attacks on your accounts.
How MFA protects your business
- Stops credential stuffing. Even if a password is leaked, the attacker still can’t log in.
- Protects remote access. Employees working off-site (where traditional corporate firewalls typically don’t apply) remain protected across devices.
- Reduces phishing risks. MFA makes email-based attacks far less effective.
- Prevents lateral movement. With MFA consistently applied, attackers can’t easily escalate privileges inside your network.
 If your business is considering biometrics as an additional factor, learn about biometric security and potential identity risks.
If your business is considering biometrics as an additional factor, learn about biometric security and potential identity risks.
Easy MFA tools for small-to-medium businesses
Choosing the right MFA tool depends on how your business operates and what systems you need to secure. Here are the most commonly used MFA tools:
- Google Authenticator: Free, widely supported, simple interface.
- Microsoft Authenticator: Integrates with Microsoft 365 accounts and supports push notifications.
- Authy: Offers multi-device sync and encrypted backups.
- Hardware keys (YubiKey, SoloKey, etc.): Physical devices that provide stronger protection for high-risk accounts.
For a more detailed breakdown of the options available, this guide to authenticator apps offers a clear comparison.
4. Keep software and systems updated
Every piece of software your business uses (operating systems, apps, plugins, even firmware) has potential vulnerabilities. The longer you wait to apply updates, the larger that attack window gets.
Automating patch management
Manual updates don’t scale. Automating patch management helps ensure nothing slips through:
- Use centralized update management tools. Platforms like Microsoft Intune or Jamf (for Mac environments) allow you to deploy patches across multiple devices automatically.
- Enable auto-updates where available. Many SaaS providers and cloud platforms handle updates automatically, which you can use to your advantage.
- Set patch windows. Schedule updates during off-hours to minimize disruption.
- Monitor compliance. Use reporting tools to verify that all systems are running the latest versions.
Commonly overlooked updates
Even companies with good patch habits often miss:
- Firmware updates on routers, firewalls, printers, and IoT devices.
- Browser plugins and extensions, which are frequent attack vectors.
- Third-party libraries used in custom apps or website backends.
- Mobile devices, both company-owned and bring your own device (BYOD) systems.
- Cloud platform security patches, including AWS, Azure, and Google Cloud configurations.
Attackers target what’s easiest: old, unpatched systems. Staying current closes that door.
5. Secure your Wi-Fi and network access
If someone gets into your network, everything behind it is exposed: email, files, customer data, and internal systems. That’s why securing your Wi-Fi isn’t just about setting a strong password and walking away. You need to treat your router and network like the front door to your business.
Creating a separate guest network
Visitors don’t need access to your business systems. The safest approach is to create a completely separate Wi-Fi network for guests, isolated from your internal network.
Keep the guest network simple: internet access only. It shouldn’t connect to your servers, printers, or any shared folders. And change the guest password regularly, especially after contractors, vendors, or temporary staff leave.
This way, even if a guest’s device is compromised, the attacker can’t easily pivot into your core systems.
Router security essentials
Most routers ship with wide-open settings that attackers love to exploit. You’ll want to tighten those defaults immediately.
- Change the default admin username and password. They’re public knowledge.
- Use Wi-Fi Protected Access 3 (WPA3) encryption if your router supports it. If not, WPA2 is still acceptable, but anything older needs to be replaced.
- Turn off features you’re not actively using, like Wi-Fi Protected Setup (WPS) or remote management.
- Update your router’s firmware regularly; this often patches serious security holes.
- Segment your network if possible. Keep your most sensitive systems (like HR files or payment systems) on a separate virtual local area network (VLAN) or subnet.
If your router is more than a few years old and doesn’t support these options, it’s likely time for an upgrade. The cost of better hardware is tiny compared to the damage of a compromised network.
6. Use a business-grade firewall and antivirus
Small businesses often rely on whatever security came pre-installed on their devices. That’s not going to hold up against modern threats. Firewalls and antivirus software aren’t just nice-to-haves; they form the baseline of any real defense.
Why built-in protection isn’t enough
Built-in tools like Windows Defender or a basic router firewall can catch some threats, but they’re not designed to deal with modern, targeted attacks. Sophisticated malware, zero-day exploits, and fileless techniques often evade signature-based antivirus. Some attacks bypass malware altogether, using misconfigured services, stolen credentials, or remote access tools.
Business-grade firewalls allow you to:
- Control which devices and services can talk to each other inside your network.
- Monitor unusual traffic patterns that may signal an attack.
- Block entire categories of risky content before employees even click.
Choosing tools for small business needs
- Next-generation firewalls (NGFWs) combine intrusion prevention, application control, and deep-packet inspection in one device, helping detect and block unusual behavior in real time.
- Endpoint detection and response (EDR) solutions actively monitor device behavior rather than relying on static signature databases. Traditionally seen as a solution for large organizations with dedicated security teams, EDR has become more accessible and SMB-friendly in recent years.
- Managed services offer turnkey protection if you lack IT staff. Many vendors now provide SMB-focused bundles that include a firewall and antivirus.
7. Back up your data regularly
No matter how strong your security is, you can’t fully eliminate risk. Ransomware, hardware failure, accidental deletion; they happen. Ransomware in particular is dangerous, as it is by far the most common and destructive cyberattack targeting small businesses. Regular backups are the one safeguard that can make the difference between a major incident and a minor inconvenience.
Cold vs. cloud backup
Generally, there are two options to pick from (although you can opt for a hybrid system as well): cold and cloud backup.
Cold backup, typically stored onsite and offline (like on external hard drives), is disconnected from the internet. Cloud backup, on the other hand, stores your data on remote servers maintained by third-party providers like Backblaze, Acronis, or Microsoft OneDrive for Business.
There are advantages and disadvantages to both options, but for small businesses, especially those that don’t have a huge volume of data to protect, it’s generally more advisable to use local, “cold” storage. The reason is simple: if your device or server can access the cloud backups, then so can the attackers who compromise your devices or servers.
This setup will prevent your backups from being encrypted by ransomware, and it also allows for faster data recovery, especially when restoring large files, and gives you complete control over how and where your data is stored. Once the hardware is purchased, there are no ongoing subscription costs either.
8. Limit access to sensitive information
A stolen account shouldn’t give an attacker free rein over your entire system. Yet that’s exactly how many breaches escalate because too many people have access to data they don’t need.
Role-based access control (RBAC)
RBAC fixes this by aligning access with responsibility. If someone’s job doesn’t require seeing payroll data, customer records, or financial reports, that door stays closed. When an attacker gets in through one compromised account, RBAC limits how far they can go. A single set of stolen credentials won’t give them access to every database or internal system you operate.
Identity and access management (IAM)
IAM systems like Microsoft Entra ID or Okta take access control further by centralizing the entire process. With IAM, you:
- Set up accounts automatically as employees join, leave, or change roles.
- Apply least-privilege rules across all cloud apps and internal systems.
- Enforce MFA for high-risk access points.
- Track who’s accessing what and when.
When permissions change automatically with job roles, mistakes disappear. And when accounts are closed the moment someone leaves, your exposure window closes with them.
9. Create an incident response plan
No business plans to get hacked. But when something breaks, it’s not the time to figure out what to do next. That decision-making needs to be done long before anything goes wrong.
An incident response plan (IRP) lays out exactly how your team will react when a breach happens.
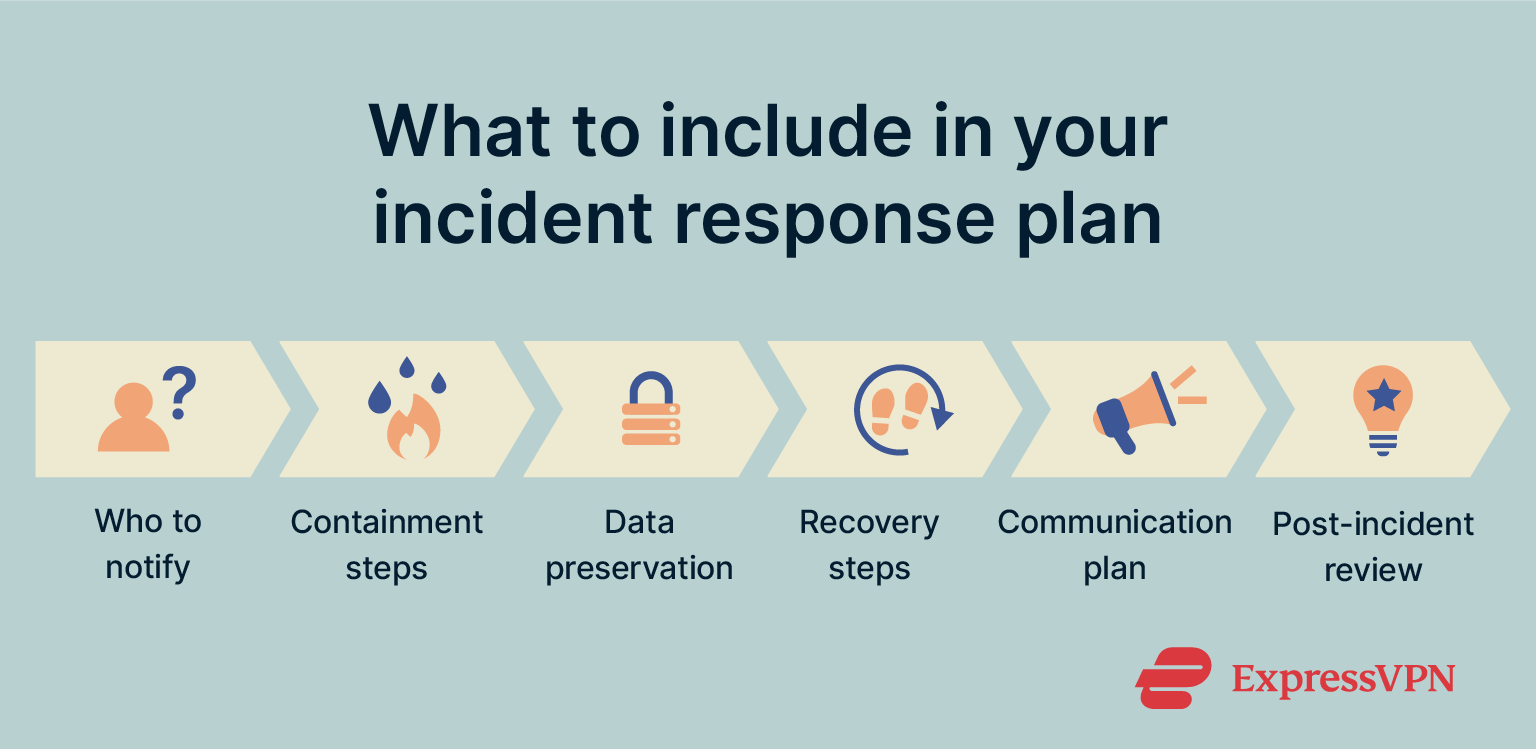
What to include in your IRP
Your plan doesn’t need to be complicated. It needs to be clear. Make sure to cover the following:
- Who gets notified: Internal contacts, outside vendors, legal counsel, and law enforcement if needed.
- Containment steps: Isolate affected systems immediately to stop further spread.
- Data preservation: Secure logs, system images, and evidence before any cleanup.
- Recovery process: Step-by-step instructions for restoring systems and resuming business operations.
- Communication plan: Who handles customer notifications, regulatory disclosures, or PR responses.
- Post-incident review: Document what happened, why it happened, and what gets fixed to prevent it from happening again.
Response plan templates for SMBs
The FTC’s Data Breach Response: A Guide for Business offers clear, actionable steps to help you respond effectively in case of a data breach. It covers how to secure compromised systems, work with forensic experts, notify affected individuals and authorities, and communicate transparently with stakeholders (the guide includes a template of a notification letter you can use for that).
10. Use a trusted VPN
Install a reputable virtual private network (VPN) on all desktop and mobile devices used for your business. A VPN encrypts your internet connection, protecting sensitive data from prying eyes, especially when using unsecured public networks. It also helps shield your business from cybercriminals who might try to intercept communications or monitor your online activities.
Choosing the right VPN provider
Not all VPNs offer the same level of protection. For business use, prioritize:
- Trusted encryption standards: Look for providers using strong, independently audited protocols.
- Scalability: Volume licensing simplifies management as your team grows.
- Consistent performance: Encryption shouldn’t cripple connection speeds or disrupt workflow.
- Reliable customer support: Issues need immediate resolution, especially if business operations are interrupted.
OPSEC: The missing piece in your cybersecurity strategy
While the tips we’ve covered lay a solid foundation, there’s one more layer that small businesses often overlook: OPSEC, or operational security. It’s a mindset that helps you identify what sensitive information you’re exposing without even realizing it, through employee habits, social media, or casual conversations. Want to take your security awareness to the next level? Learn how OPSEC can protect your business.
FAQ: Common questions about cybersecurity for SMBs
What is the most common cyber threat for small businesses?
Ransomware remains the biggest threat, often locking businesses out of critical data until a ransom is paid. Phishing is also widespread, tricking employees into giving up credentials or downloading malware. Both threats usually exploit simple mistakes rather than sophisticated technical flaws.
How often should I update my cybersecurity strategy?
As a baseline, review your cybersecurity strategy at least once per year and immediately after any major changes, like new systems, remote work setup, vendor integration, or handling new types of sensitive data.
What are affordable cybersecurity tools for small businesses?
Plenty of budget-friendly options offer strong protection. Password managers secure account access, while multi-factor authentication (MFA) blocks most unauthorized logins. Business-grade antivirus and firewalls help prevent malware and ransomware. Cloud backups ensure quick recovery after data loss, and a trusted virtual private network (VPN) protects internet traffic. Combined, these tools cover most security gaps.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN