What is doxxing, and how can you stay safe online?

Imagine waking up one day to find your real name, home address, phone number, and maybe even where you work blasted all over the internet for anyone to see. It’s not just embarrassing; it’s dangerous.
It doesn’t take a hacker or a private investigator. With enough digging, a stranger can piece together bits of your life from old posts, public records, and forgotten accounts. Once your information is out there, you don’t get to choose who sees it or what they do with it.
This guide will show you what’s behind it, why it happens, and, most importantly, how you can protect yourself.
What does doxxing mean?
Doxxing (also spelled as “doxing”) is the practice of sharing someone’s private information without that person’s permission. It’s not always high-tech; a lot of the time, it’s about piecing together information that’s already out there: old forum posts, social media profiles, public records, even online purchases. The goal isn’t just to find information. It’s to use it to embarrass, intimidate, harass, or harm the person being exposed. You don’t have to be a celebrity or a public figure to be doxxed. Regular people get targeted, too, sometimes over personal arguments, political opinions, or even random online encounters.
You don’t have to be a celebrity or a public figure to be doxxed. Regular people get targeted, too, sometimes over personal arguments, political opinions, or even random online encounters.
Where does the term doxxing come from?
The word “doxxing” comes from “docs,” short for “documents.” In the early days of online forums and hacking communities, “dropping docs” on someone, meaning leaking their real-world identity, was a way to take revenge or settle scores. Over time, “dropping docs” became “doxxing.”
It started in the 1990s, when internet anonymity was the norm. Exposing someone’s real identity wasn’t just an attack; it was seen as the ultimate betrayal of online privacy. Today, the tactics are more sophisticated, and the internet is not as private as it used to be to begin with, but the idea is the same: take what someone didn’t intend to share and force it into public view.
Is there a difference between doxxing and leaking?
Both doxxing and leaking involve putting private information out in public, but they’re used in different contexts.
Leaking usually means sharing confidential information from inside a company, government, or other organization. It’s often about exposing hidden practices, not going after a specific person. Think of whistleblowers revealing corruption or secret documents getting out.
Doxxing is personal. It’s about digging up details about someone’s life, like where they live, who their family is, or where they work, and posting it online to shame, scare, or hurt them. One goes after systems, while the other goes after people.
How does doxxing work?
Most of the time, doxxing is about pulling together small pieces of information that people leave scattered across the internet. A doxxer might start with a username, an email address, or a social media post and then follow the trail.
They can search public records, dig through social media activity, scan old forum posts, or even use tricks like phishing to get even more personal data. Some go further, using technical tools to track IP addresses or pulling information from databases that collect and sell personal details.
Piece by piece, they build a profile. And once they have enough, they can expose that information online, putting the target at risk of harassment, identity theft, or worse.
Let’s break down the most common ways people get doxxed.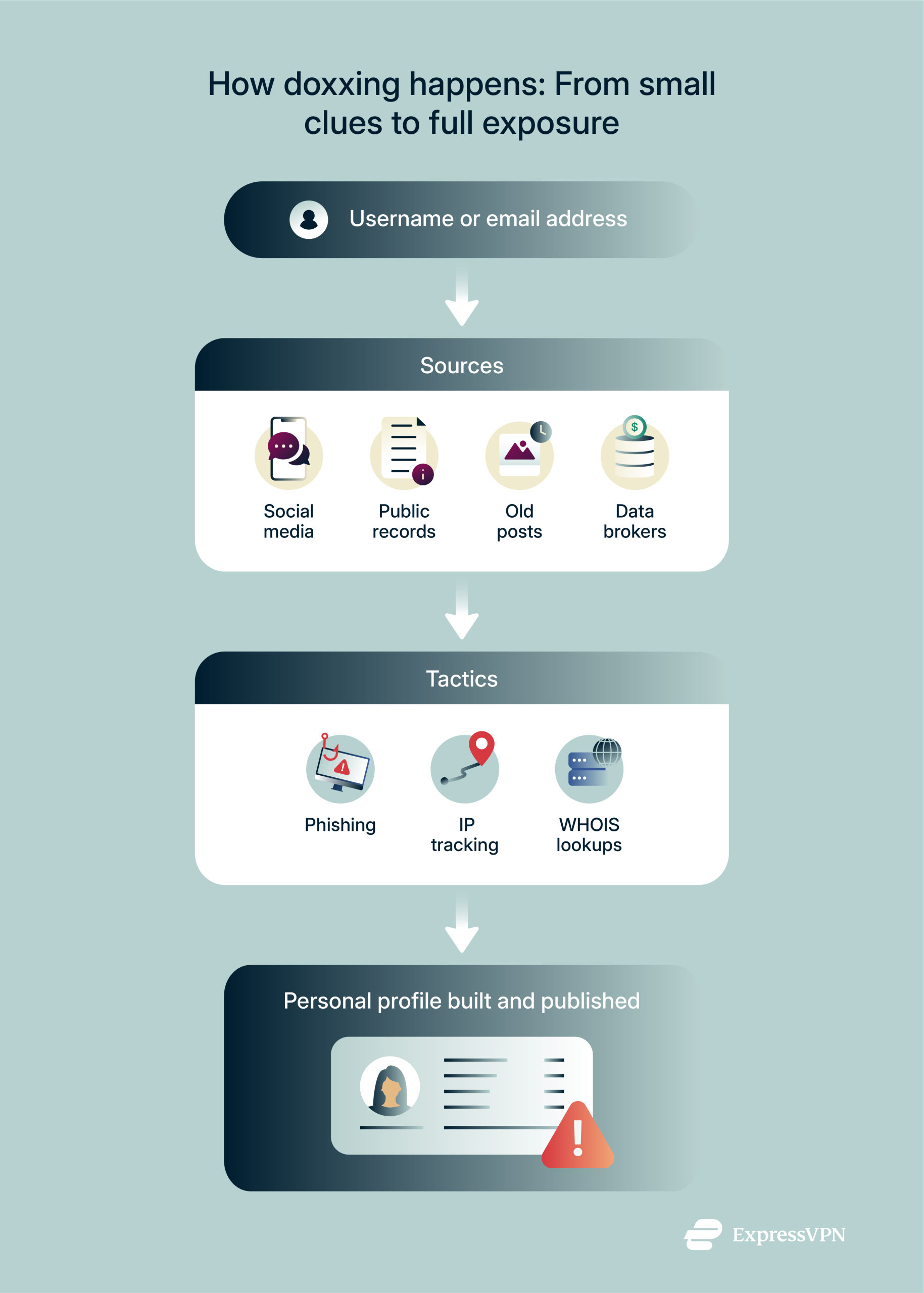
Tracking usernames across platforms
A doxxer might start by spotting your username on one platform, then search for it elsewhere. Maybe a gaming profile leads them to a social media page. Maybe an old post reveals an email address or hints at where you live. On their own, these details don’t seem like much. But stitched together, they can give away more than you think.
Running WHOIS lookups on domain names
When you register a domain name, your personal information, like your name, email address, phone number, and even home address, can end up in public records through what’s called a WHOIS database.
A doxxer can easily run a WHOIS lookup on a domain to see if any personal details are attached. If the domain wasn’t registered with privacy protection, that information can be visible to anyone who knows where to look.
Using domain privacy services when registering websites is one of the simplest ways to keep this kind of information out of public view.
Using phishing to trick people into revealing info
Phishing is a common tactic doxxers use to trick people into giving up personal information. Instead of breaking into your accounts, they rely on fooling you into handing over details yourself.
This can take the form of fake emails, messages, or websites that look legitimate, like a spoofed login page for your email or social media account. You might receive a message claiming there’s been suspicious activity on your account, prompting you to click a link and “verify your identity.” If you follow through and enter your credentials, the attacker now has access.
Some doxxers go further by impersonating authority figures or customer service agents to pressure their targets into sharing sensitive information, like addresses, phone numbers, or even answers to security questions. These details can then be used to dig up more personal data or to access other accounts.
Mining data from social media
Doxxers might dig through old posts, tagged photos, public comments, or even friend lists to gather small pieces of information. Over time, these details can be combined to create a full profile, which is enough to find your home address, phone number, or get into your other online accounts.
Even simple posts can open the door. A photo might reveal your neighborhood. A graduation post might show your school. A “throwback” post might expose your maiden name or past addresses. Locking down privacy settings and being careful about what you share publicly can make it much harder for someone to use your own posts against you.
Locking down privacy settings and being careful about what you share publicly can make it much harder for someone to use your own posts against you.
If you want to see just how much can be uncovered from social media alone, here are four ways people can be identified through their posts. It’s eye-opening, and a good reason to double-check what you’ve shared.
Searching public and government records
If you’ve ever owned property, registered to vote, filed a lawsuit, or started a business, there’s a good chance your information is sitting in a public file somewhere.
Doxxers usually don’t need to hack anything; they can simply search public databases to dig up important details. They often look through:
- Property records: Revealing home ownership and addresses.
- Court filings: Exposing legal disputes, lawsuits, and family issues.
- Marriage licenses and voter registrations: Connecting names, addresses, and even family relationships.
- Business licenses: Showing where you work or what you own.
Tracking IP addresses
Every time you connect to the internet, you leave behind an IP address, which doxxers can use to get a rough idea of where you’re located, like your city or neighborhood.
Some doxxers might even use IP addresses to try to launch attacks, like overwhelming your network with traffic, known as a distributed denial-of-service (DDoS) attack, or scanning for other vulnerabilities
Using a VPN can hide your real IP address and make it much harder for anyone to track you this way.
Leveraging data brokers
Data brokers are companies that collect personal details, like names, home addresses, job history, shopping habits, and even hobbies, from public records, online tracking, and third-party sources.
Once collected, this information is packaged and sold, often without you ever knowing. For a few dollars, anyone, including a doxxer, can buy a report that links your online activity to real-world facts about your life.
The good news is that you can ask a data broker to remove your information from their databases. The bad news? You have to request this separately from each data broker that has your data, and that could mean dozens. Controlling what data brokers have on you isn’t easy, so a service like ExpressVPN’s Identity Defender (U.S. only) can be very helpful.
What type of information do doxxers target?
Common targets include:
- Full names, home addresses, phone numbers, and email addresses;
- Birthdates;
- Social media profiles, revealing workplaces, routines, friends, and family;
- Photos where background details like street signs or badges can give away location;
- Financial information or account details, exposing banking or billing records;
- Old usernames and online accounts, linking different parts of your digital life together.
The real danger, however, isn’t any single piece of information; it’s how everything fits together. A home address plus a workplace, a birthday paired with an old phone number. These links make it easier for someone to find you, impersonate you, or cause harm in real life.
Why do people engage in doxxing?
Sometimes, doxxing is personal, meant to hurt or humiliate. Other times, it’s used to call someone out or make a statement. Whatever the reason, the goal is usually the same: to put pressure on someone by exposing their private information.
Revenge or harassment
Doxxing is commonly used to get back at someone, like a former friend, an ex, or a rival from an online argument. Publicly posting someone’s private information can make them feel exposed, vulnerable, and unsafe.
This kind of doxxing often follows heated interactions online, like arguments in comment sections, gaming communities, or social media threads. It can escalate quickly, moving from name-calling to finding and posting private details.
Activism or exposure
Not all doxxing is driven by revenge. In some cases, it’s used to draw attention to a person’s actions. Especially when those actions are seen as harmful, offensive, or unethical. The idea is to expose someone, often in the name of accountability.
This kind of doxxing shows up in activism, online call-outs, or attempts at “vigilante justice.” It might involve revealing the identity of someone caught on video behaving badly, sharing harmful views, or being accused of serious misconduct.
While some see it as a way to hold people responsible, it still puts private lives in the spotlight, and the fallout can be serious, even when the original intent is to inform rather than harass.
Is doxxing illegal?
Sharing personal information isn’t always against the law, especially if it’s public. Laws vary by country and even by state. Some have clear rules against doxxing, while others use broader laws around harassment or stalking. And even if it’s not illegal, most platforms ban it. Getting doxxed can still lead to serious fallout, whether charges are filed or not.
Doxxing crosses the line when it moves from sharing information to causing harm or intending to do so. If the intent is to threaten, harass, blackmail, or encourage others to act violently, it can be treated as a criminal offense.
It also depends on how the information was gathered. Some clear examples where doxxing crosses the line include:
- Hacking into private accounts: Breaking into someone’s private email, social media, or cloud storage is illegal.
- Using stolen data from breaches or illegal sources: Sharing or weaponizing information that was obtained through hacking, leaks, or black-market databases adds criminal charges to the act of doxxing.
- Using public information to stalk, intimidate, or endanger someone: Even data from public records can be used illegally if the purpose is harassment, stalking, or threatening someone’s safety.
When any of these actions are involved, doxxing stops being just an invasion of privacy. It becomes a legal issue, and in many cases, a criminal one.
How to know if you’ve been doxxed
Sometimes, doxxing is loud; your phone blows up with threats, or someone posts your address in a comment thread. Other times, it’s quieter. A stranger suddenly knows your real name. An old photo resurfaces. A friend asks why someone contacted them out of the blue.
Here are some signs to watch for:
Unusual account activity
Strange things happening on your accounts can be an early warning sign. Maybe you get alerts for logins you didn’t make, password reset emails you didn’t request, or messages that were sent without your knowledge.
Read more about what to do if you think your social media account has been hacked here.
Receiving threats or harassment
Sudden messages from strangers, aggressive comments, or creepy DMs might not be random. Harassment is one of the most obvious signs of doxxing, especially if it’s targeted, persistent, and personal.
If you’re worried about younger family members, spotting the signs of cyberbullying early can make a big difference.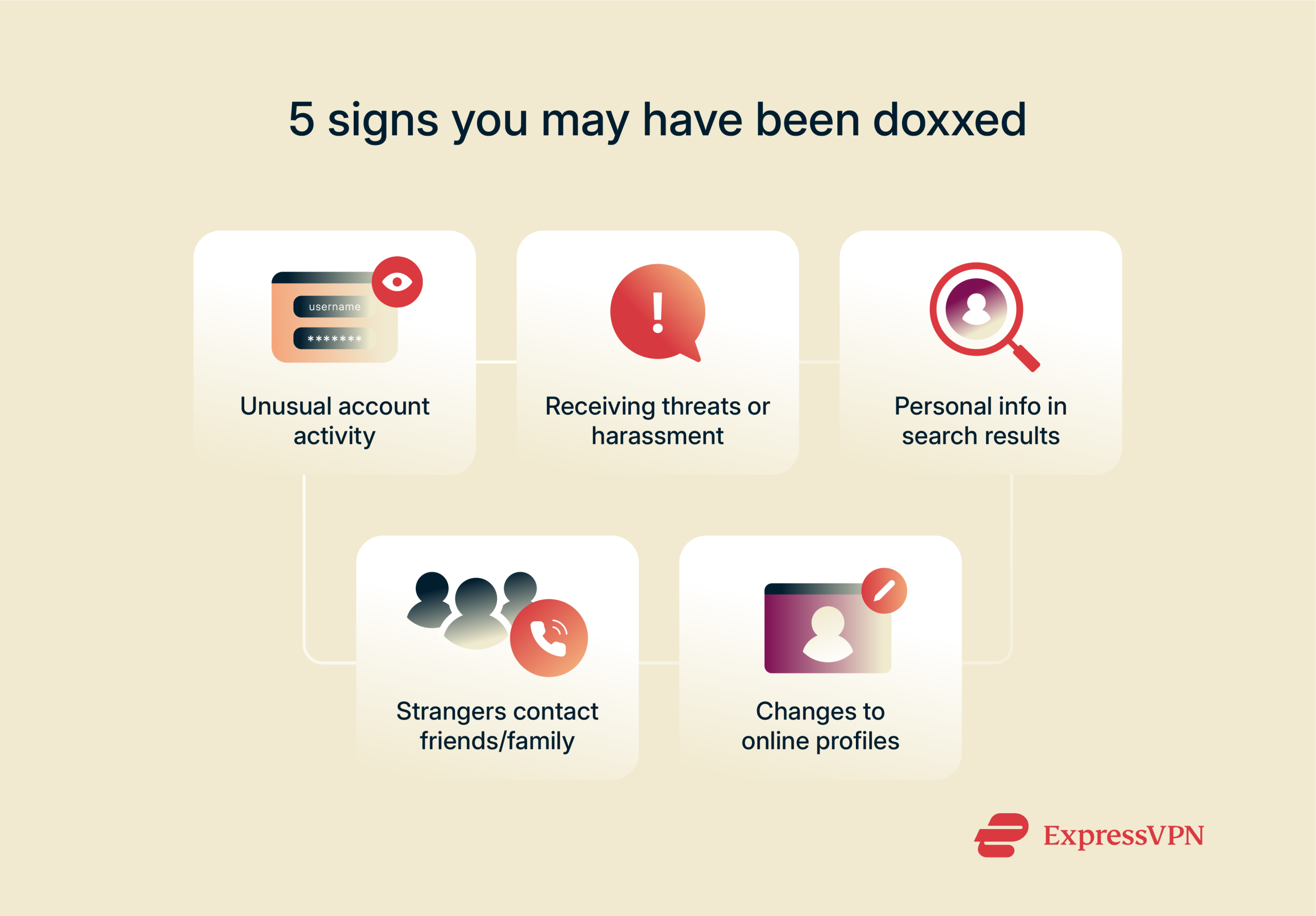
Personal info appears in search results
If your name, address, phone number, or other private details start showing up in search engines, forums, or public posts, and you didn’t put them there, that’s a red flag.
Friends or family are contacted by strangers
If people you know start hearing from strangers asking about you or saying something feels off, there’s a good chance your information has been shared. This tactic is often used to dig deeper or cause panic.
Changes to your online profiles
If someone gains access to your accounts, they might change your profile picture, bio, or email or even post content pretending to be you. These kinds of changes are usually meant to confuse, impersonate, or provoke, and they’re a serious sign that something’s wrong.
Real-world examples of doxxing
Doxxing isn’t just a headline term; it’s caused real harm to real people. Here are a few well-known cases that show how far it can go.
Boston Marathon bombing misidentification
After the 2013 Boston Marathon bombing, users on Reddit tried to help the authorities identify the culprits. But instead of helping, they ended up falsely accusing an innocent person, a missing student named Sunil Tripathi.
His name and photos spread fast across social media and news sites, leading to harassment of his family during an already devastating time (Sunil had been missing for weeks and was later found to have died by suicide).
The case became a major example of how quickly online crowdsourcing can spiral into real-world harm when personal information is shared without proof.
Keffals’ swatting and harassment
In August 2022, Twitch streamer and activist Clara Sorrenti, better known online as Keffals, was the target of a swatting attack. Someone impersonated her in a fake email to city officials in London, Ontario, claiming she had harmed her family and was planning more violence. It led to police raiding her home at gunpoint.
The attack wasn’t random; it was part of a larger harassment campaign tied to her activism, fueled by people who had already doxxed her.
After the raid, Keffals went public with her story, calling out the dangers of online harassment and pushing for action against forums like Kiwi Farms, where much of the targeting had started.
YouTubers clash after doxxing incident
In October 2023, things got personal between YouTubers SSSniperwolf (Alia Shelesh) and Jacksfilms (Jack Douglass). After some ongoing public criticism, Shelesh posted a photo of Douglass’s house on Instagram with a caption suggesting she might stop by.
Douglass accused her of doxxing, shared the post publicly, and pushed YouTube to respond. A few days later, the platform suspended Shelesh’s monetization, saying her actions broke their safety rules. Shelesh apologized and admitted she should’ve handled it differently.
The situation was a reminder that even internet drama has real-world impact, and platforms are being watched closely to step in when things go too far.
How to protect yourself from doxxing
You can’t control everything online, but you can make yourself a much harder target. Doxxers usually look for easy wins, people who leave a clear trail behind. With a few smart habits, you can lock down your information and make it a lot harder for someone to dig into your private life.
| Step | What to do | Why it matters |
| 1 | Use a VPN like ExpressVPN. | Hides your IP and location from prying eyes. |
| 2 | Don’t use your real name online. | Makes it harder to link your identity to your activity. |
| 3 | Audit your digital footprint. | Helps you find and clean up personal info that’s already out there. |
| 4 | Lock down social media settings. | Prevents strangers from seeing where you live or work. |
| 5 | Use multi-factor authentication (MFA). | Adds a second verification step to protect your accounts. |
| 6 | Use different emails for different accounts. | Stops one leak from exposing everything. |
| 7 | Use strong, unique passwords. | Makes it harder for anyone to break into your accounts. |
| 8 | Avoid sketchy apps and online quizzes. | They can quietly collect sensitive info. |
| 9 | Search your own name. | Helps you see what others might find. |
| 10 | Set Google Alerts for your name. | Gives you early warning if your info pops up online. |
Use a VPN to mask your IP address
As mentioned above, a VPN hides your real IP address by routing your internet traffic through a secure, encrypted server. Using a VPN helps keep your online activity private and makes it much harder for someone to connect what you do online to your real-world identity, especially when using unsecured networks.
Don’t use your real name online
The more you link your real name to your online activity, the easier it is for someone to track you down. Doxxers look for small clues that connect a username, an email, or a post to a real identity.
One of the best ways to protect yourself is to use different usernames that don’t include your full name, birthday, or anything else personal. If a site doesn’t really need your real name, don’t give it. Keeping that separation makes it a lot harder for someone to build a complete profile on you.
Audit your digital footprint regularly
You might be sharing more than you realize. Old social media posts, forgotten accounts, online comments, all of it can leave a trail. Doxxers are good at digging through that history to find connections and personal details.
Make it a habit to search your own name and usernames every so often. See what comes up. Delete old accounts you don’t use, tighten your privacy settings, and remove anything that gives away more about you than it should.
Secure your social media profiles
Take control of your privacy settings by:
- Limiting who can see your posts: Choose friends-only or custom settings instead of public.
- Hiding your friend lists: Keep connections private to protect your social circle.
- Avoiding real-time updates: Wait to post about vacations, events, or outings until after the fact.
Want help adjusting your Facebook settings specifically? Check out this step-by-step guide to Facebook’s latest privacy tools.
Enable multi-factor authentication
Multi-factor authentication (MFA) adds an extra layer of protection to your accounts. Even if someone manages to get your password, they would still need a second verification code, often sent to your phone or generated by an app, to get in.
Create separate emails for different uses
One email address for everything makes it easy for you… and for anyone trying to track you. If a doxxer gets your main email, they can quickly find accounts, posts, and profiles connected to it.
Using separate emails for different aspects of your life helps break those links. Keep one address for personal communication, another for work, and a different one for anything public, like social media, forums, or gaming. That way, even if one email gets exposed, it doesn’t open the door to your whole online life.
Use strong, unique passwords
Weak passwords are an open door for attackers. If you reuse the same password across sites, getting hacked once can mean getting hacked everywhere.
Use passwords that are long, random, and hard to guess. Don’t lean on easy patterns like birthdates, pet names, or anything someone could figure out by looking at your social media.
Using a password manager like ExpressVPN Keys is the best way to generate and store passwords safely.
Be careful with online quizzes and permissions
Not every threat looks like a threat. Sometimes, it’s a fun quiz or a harmless-looking app asking for a little too much access. Those “What’s Your Spirit Animal?” quizzes or random polls can quietly collect personal information, like your name, your location, or even clues to your passwords and security questions.
Check how easy it is to dox yourself
Sometimes, the best way to spot a problem is to think like a doxxer. Search your name, usernames, and email addresses and see what comes up. You might be surprised at how much information is already out there, including old profiles, forgotten posts, or bits of personal data tied to your online activity.
The goal isn’t to scare yourself. It’s to find weak spots before someone else does. If you spot something you don’t want public, take steps to remove it, lock it down, or update your privacy settings.
Set up Google Alerts for your name
You can’t watch every corner of the internet yourself, but Google can help. Setting up Google Alerts for your name, email addresses, or other important details lets you know if something new pops up online.
It’s not a perfect system, but it gives you a head start. If you want to go further, here are a few simple privacy habits worth picking up.
What to do if you’ve been doxxed
Finding out your personal information has been exposed can feel overwhelming, but acting quickly can make a big difference. The goal is to slow the spread, protect yourself, and document what’s happening in case you need legal or platform support later.
Report the doxxing to platforms and authorities
Start by reporting the posts or content to the platforms where the information was shared. Most major sites, like Facebook, X, and Reddit, have policies against sharing personal information and will remove it if you report it.
If the doxxing involves serious threats or harassment, contact local law enforcement. Share as much information as you can, including screenshots and links. Even if it feels overwhelming, reporting early helps build a record in case the situation escalates.
Document everything as evidence
When you see that your information has been shared, don’t just report it; save it. Screenshots, URLs, and timestamps: grab everything you can while it’s still live. Doxxers often delete posts once they know they’ve been spotted, but if you’ve already saved the evidence, it’s still yours to use.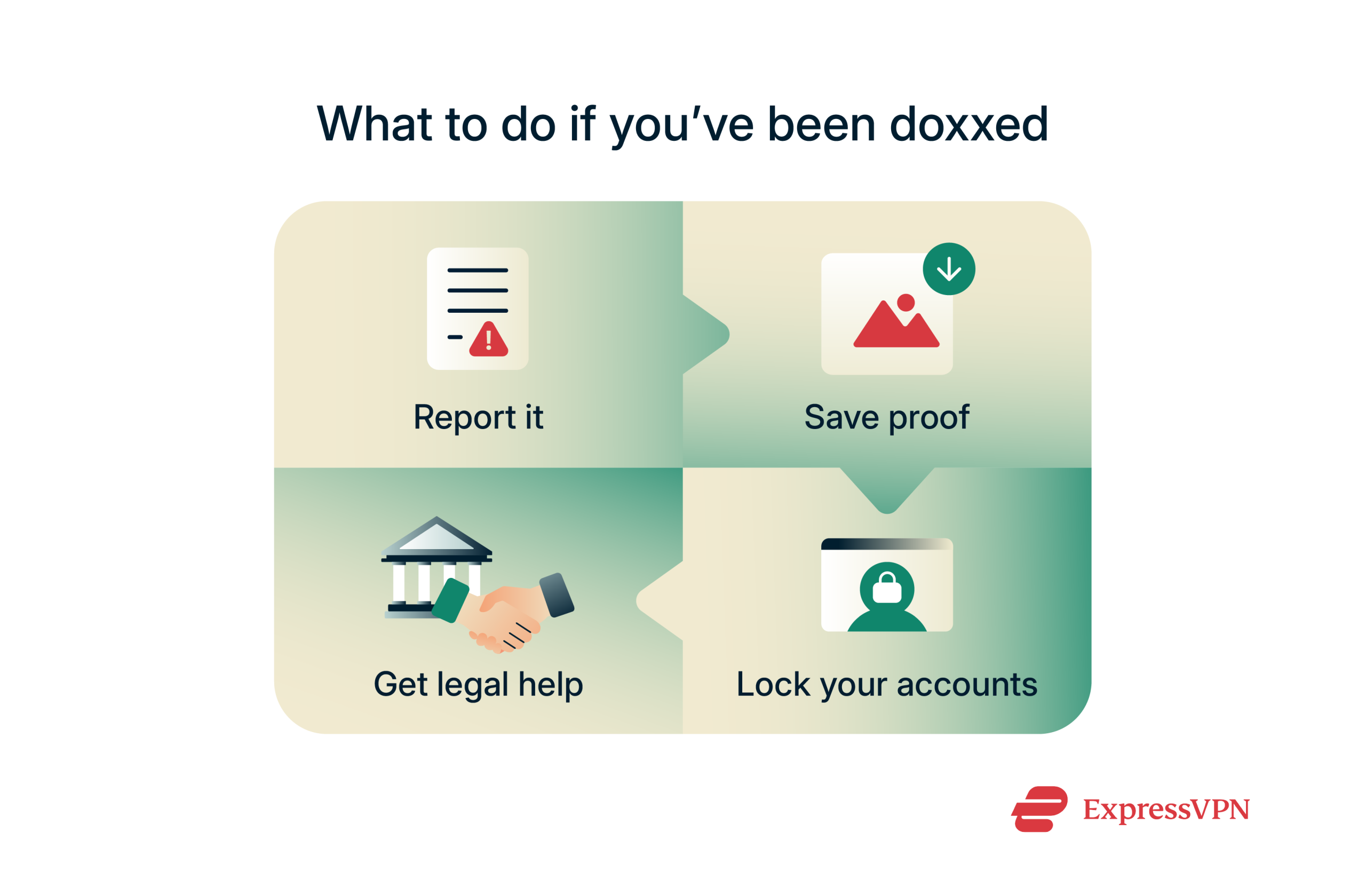
Fortify your online accounts
If someone is targeting you, your accounts are the next thing they’ll go after. Change your passwords right away, starting with your email, social media, and anything tied to your identity. Turn on MFA if you haven’t already.
Consider a digital privacy service or legal help
Sometimes, cleaning up after a doxxing attack is bigger than one person can handle. Privacy services like the one included with every U.S. ExpressVPN subscription can help remove your information from data broker sites and monitor for new leaks.
If things escalate, especially if there are threats involved, talking to a lawyer can give you a clearer idea of your rights and next steps.
You don’t have to face it alone. Getting the right support can make the process faster, safer, and a lot less overwhelming. And it’s not just about peace of mind; keeping your personal information out of the wrong hands can also protect you financially. Here’s how privacy and anonymity tie directly into financial safety.
FAQ: Common questions about doxxing
Is it doxxing if the info is public?
Is exposing someone’s username considered doxxing?
Can businesses or influencers be doxxed?
What is doxxing slang for?
Can you sue someone for doxxing you?
Can you protect yourself from doxxing?
Can you go to jail for doxxing?
It often comes down to intent. Posting someone’s personal information to intimidate, blackmail, or encourage others to target them is far more likely to be considered a crime, especially if it results in danger to that person’s safety.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN