DNS hijacking and how to prevent it

Domain Name System (DNS) hijacking is a cyberattack that silently reroutes your internet traffic. Attackers can use this tactic to steal sensitive data, inject malware, display unwanted ads, or block access to specific sites.
You might notice the signs if you know what to look for. For example, a favorite shopping site suddenly looks strange, or your banking credentials stop working. These issues might sound like glitches, but they could be a sign of a serious security breach.
In this article, we explain how DNS hijacking works, why it happens, and what you can do to protect yourself. Whether you browse from home, manage a site, or work remotely, this article will help you stay secure.
What is DNS hijacking?
DNS hijacking, also known as DNS redirection, is a cyberattack in which threat actors alter your DNS requests. It’s a silent attack that can change how your device connects to the internet and allow a third party to intercept your internet traffic, with potentially devastating consequences.
How DNS hijacking works
DNS is like the internet’s phonebook. It translates human-friendly domain names like “example.com” into IP addresses that computers use to identify each other on the internet. When you type a web address, your device asks a DNS server to find the correct IP, then connects you to that site.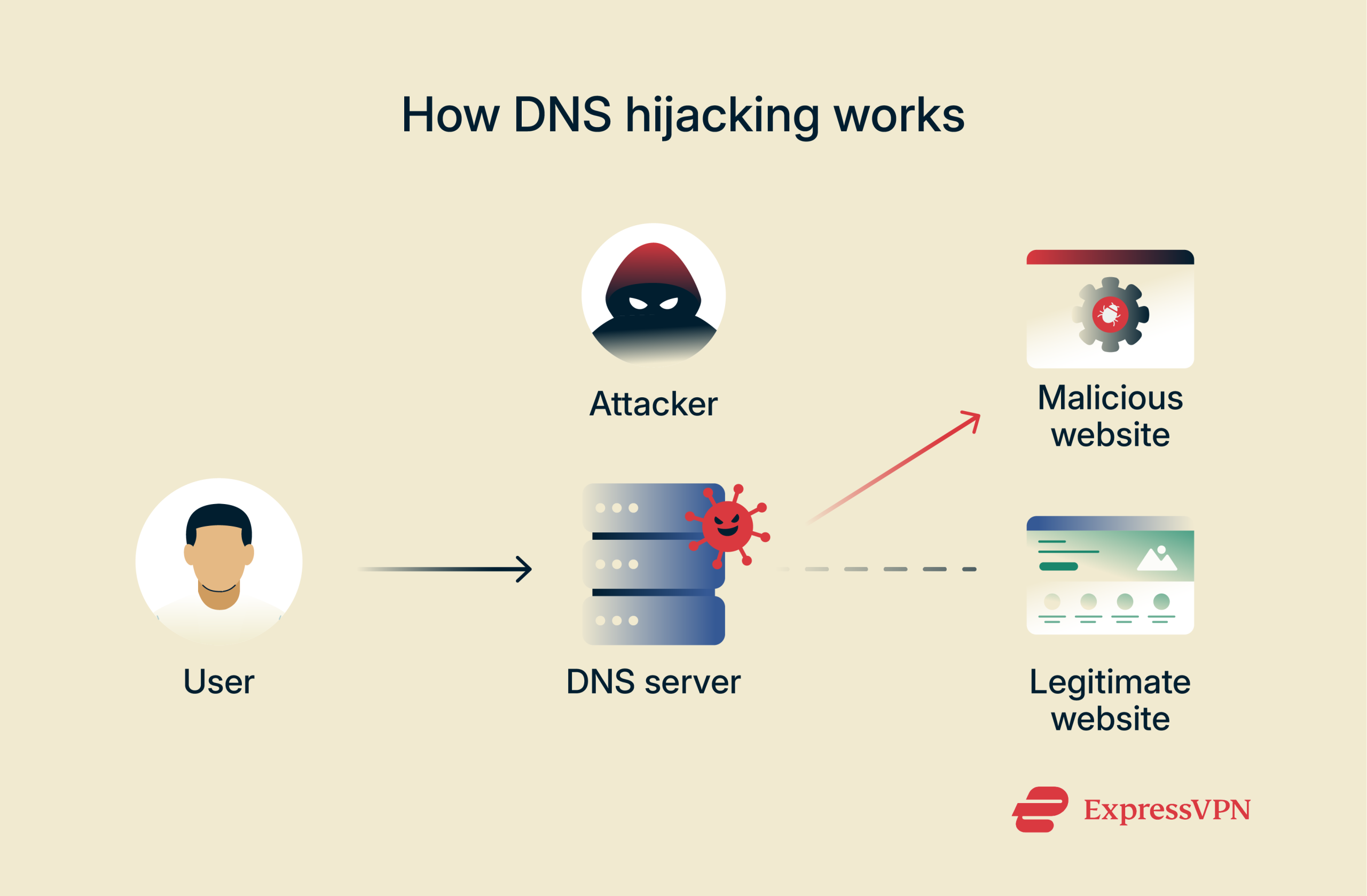 However, in a DNS hijacking attack, threat actors compromise DNS settings to swap out the legitimate IP address for one they control. This means when someone enters “sampledomain.com” into their browser, they won’t land on the real site but will be redirected to a malicious site operated by the attacker.
However, in a DNS hijacking attack, threat actors compromise DNS settings to swap out the legitimate IP address for one they control. This means when someone enters “sampledomain.com” into their browser, they won’t land on the real site but will be redirected to a malicious site operated by the attacker.
Like most cyberattacks, DNS hijacking can affect anyone connecting to the internet, whether at home, using a public Wi-Fi network, or managing a company’s infrastructure. That’s because threat actors can target home routers, unsecured networks, or internet service providers.
Why are DNS servers hijacked?
DNS servers are hijacked for various reasons. Here are a few of the most common ones.
Cybercriminal motives: Stealing personal information
Criminals use DNS hijacking to redirect you to a legitimate-looking website. For example, you launch your web browser to visit your bank account online, like you did thousands of times before. However, since your DNS requests were intercepted or the attacker has poisoned the DNS server responding to you, you end up on a site that clones your bank’s official site. Once you enter your login details, that information is harvested.
In some ways, DNS hijacking works similarly to phishing attacks, as the cybercriminal aims to route you to a malicious website to steal your login credentials. However, DNS hijacking is more sophisticated because there are often no signs to indicate you’ve landed on a fake page.
Generating revenue through malicious ads
Malicious actors use DNS hijacking to inject ads into the websites you visit or redirect you to affiliate or scam pages.
Forcing you to see and click through more ads might sound annoying rather than worrying, but these types of attacks often grow into more damaging schemes. For example, the ads you see might take you to a malware-infected download or a fraudulent website that can compromise your device’s security.
Even if the redirect is to a legitimate site, it’s often the case that the legitimate company has been scammed by a disreputable ad network that has promised them heaps of views for a low cost and then used redirect tactics to achieve it.
Government and organizational censorship
DNS hijacking isn’t just for cybercriminals. Some governments use this type of online traffic manipulation for censorship and surveillance. By blocking DNS requests, governments can prevent users from visiting specific websites, news platforms, messaging apps, or any content they feel is inappropriate.
Even internet service providers can use a type of DNS hijacking to collect DNS requests and statistics or to serve ads when users access an unknown domain. This often happens when a user mistypes a domain; instead of returning an error code, some ISPs redirect the user to a branded search page or advertisement. This is called NXDOMAIN redirection.
Common types of DNS hijacking attacks
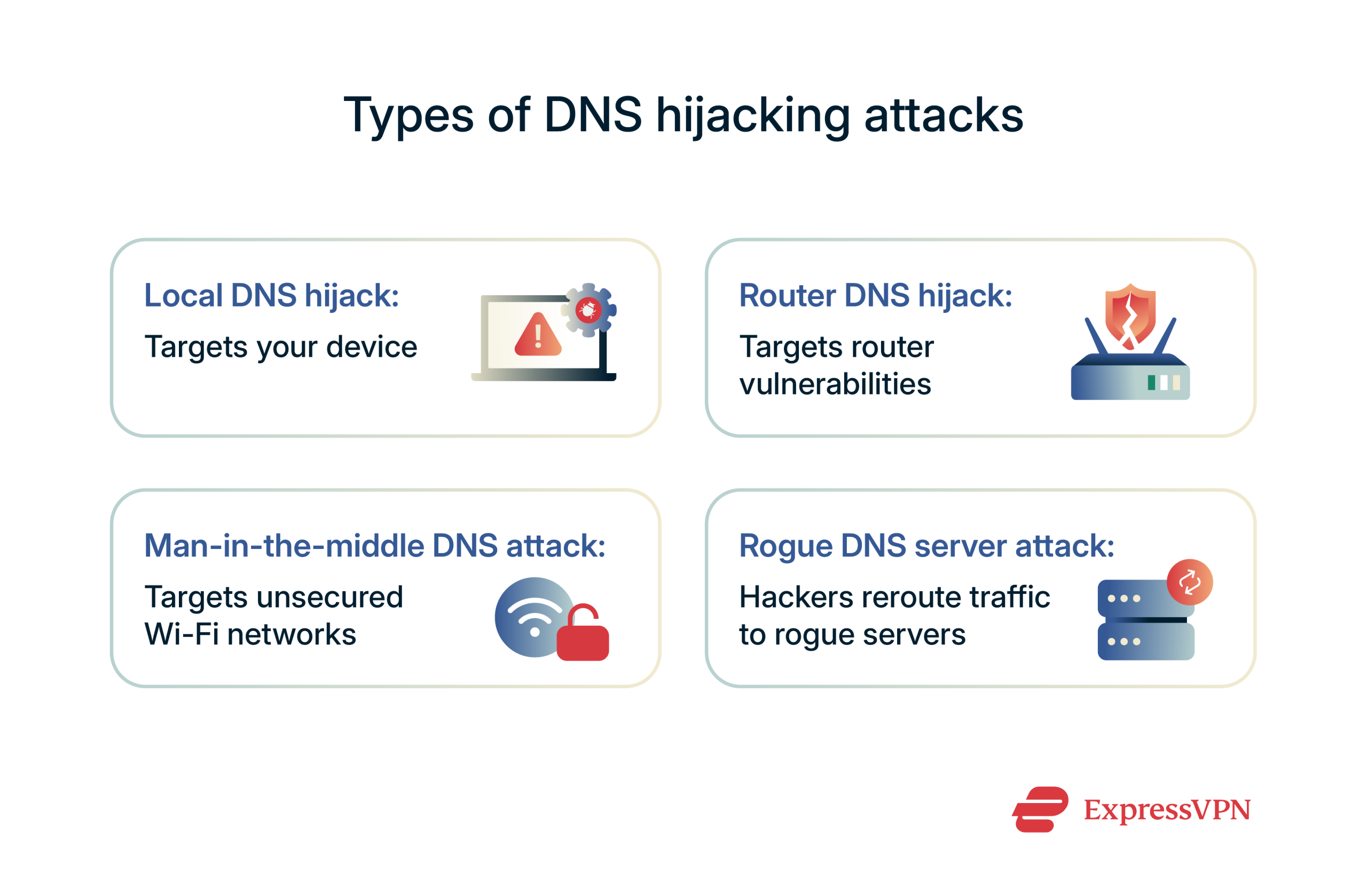
Local DNS hijack
This type of attack targets the user’s device. Attackers often use malware bundled with shady downloads to modify the system’s DNS settings. This process happens entirely in the background, meaning the user never knows the settings were changed.
Router DNS hijack
Your router is the core of your internet connectivity, meaning that vulnerabilities can have grave consequences. Common entry points for a router DNS hijack include weak router admin credentials, unpatched firmware, or open remote access ports.
One way to prevent this type of DNS hijacking is to use a VPN router app like ExpressVPN’s, which adds a layer of strong VPN encryption and DNS protection at the network level.
Man-in-the-middle (MITM) DNS attacks
In an MITM attack, malicious actors position themselves between your device and the DNS resolver, often on unsecured public Wi-Fi networks like those in coffee shops, airports, and hotels. This attack intercepts DNS requests in transit, which allows the attacker to alter responses before they reach your browser.
Once again, a VPN can be a highly effective way to prevent MITM attacks, as it encrypts incoming and outgoing data. You can learn more about this type of DNS hijacking in ExpressVPN’s MITM guide.
Rogue DNS server attacks
This is the most stealthy form of DNS hijacking. Threat actors create rogue DNS servers and route the victim’s traffic through those servers by implanting malware on their device. This means that every site the victim tries to visit is routed through the attacker’s server, which can log and track queries, block websites, inject ads and malicious code, and more.
Many home routers offer DNS-related privacy technologies, such as DNS over HTTPS (DoH) to encrypt DNS queries, while enterprise setups rely on DNS over TLS (DoT) for the same purpose.
How to detect DNS hijacking
DNS hijacking is designed to be stealthy, but there are ways to detect whether your queries are resolved maliciously. Let’s review some of them.
Use the ping command
The ping command doesn’t confirm hijacking on its own, but it can be a first step in checking basic connectivity and DNS resolution. To do this test, open your Terminal (macOS) or Command Prompt (Windows) and type: ping examplesite.com.
You’ll see a series of responses that show the contacted IP address. You can check that IP address using IPinfo.io to see who owns it. If you contacted Google’s domain, it should say that the IP you contacted belongs to Google or Alphabet, Google’s parent company. If it lists another owner, there might be something wrong.
Check DNS settings on your router
Since many DNS hijacking attacks focus on a router, it’s wise to check whether your router uses a trustworthy DNS resolver. You can do that by opening your web browser and using your router’s IP address to access its dashboard. You can usually go with 192.168.1.1 or 192.168.0.1, but it’s best to check your router’s manual.
Then, navigate to DNS settings, often under WAN, Internet, or DHCP settings. You’ll see a string of numbers: you can check whether those numbers match your IP, Cloudflare’s DNS (1.1.1.1), or Google’s DNS (8.8.8.8).
You can always change your DNS to a more trustworthy option. Another option is resetting your router and restoring its factory settings.
Use whoismydns.com to verify DNS integrity
WhoIsMyDNS is a simple but effective tool for checking how your DNS queries are resolved. To use it, just visit whoismydns.com using your web browser. After a few moments, you’ll see the information about your resolver and the DNS host. If you don’t recognize the company, that could signal that your DNS has been hijacked.
The most common warning signs include hostnames tied to suspicious internet service providers, ad networks, or unknown entities. If you notice anything strange, visit your device’s DNS settings and restore them to their default values.
Check if URLs redirect unexpectedly
Redirects are the most common symptom of DNS hijacking, taking over your DNS queries to lead you to malicious websites. Also, malicious actors can implant pop-ups, banners, and other page elements by re-routing your DNS traffic as you browse.
To check if a URL redirects unexpectedly, watch your browser’s address bar. For example, type “google.com” and check how that domain is resolved. It’s normal for it to change a bit; for example, if you browse on macOS’ Safari, it could change to “google.com/?client=Safari.” However, no drastic changes should occur, like being redirected to a completely different domain or landing on a page that doesn’t look like Google’s home page.
Also, watch out for strange-looking banners or pop-ups when browsing your frequently visited websites. These malicious page elements usually take up a large portion of the screen and urge you to scan your device for malware or something similar.
How to prevent a DNS hijacking attack
Preventing DNS hijacking requires a layered approach, because this type of cyberattack can target multiple levels, from your device to a domain registrar. Let’s walk through a series of actionable tips.
Prevention tips for general internet users
Whether you’re browsing from home or on public Wi-Fi, here’s how to reduce your exposure to DNS hijacking:
- Use a trusted DNS provider: You can always change your device’s default DNS, even if there’s no reason not to trust your internet provider. A trustworthy DNS provider can help filter malicious domains and provide additional protections, such as DoH and DoT. Some of the best options include Cloudflare (1.1.1.1) and Google DNS (8.8.8.8).
- Use a VPN with encrypted DNS: Aside from using a reputable DNS provider, the best thing you can do for your online privacy is to use a VPN. ExpressVPN comes with fully encrypted DNS, routing your traffic through private DNS servers, adding encryption, and preventing tampering.
- Check your router and device DNS settings: Make a note of your current DNS addresses so you can see if they can get changed in the future. Remember that you can always revert them back or use trustworthy DNS servers like Google’s (8.8.8.8).
- Keep your operating system patched: Outdated OS versions and firmware provide an entry point for criminals, who use vulnerabilities to make unauthorized changes. Make sure to update your operating system and apps, and set your router to auto-update its firmware if possible.
- Be wary of open public Wi-Fi networks: Threat actors often use unprotected public networks to execute MITM attacks. To prevent this type of manipulation, use public Wi-Fi only when connected to a VPN server. Furthermore, a capable antivirus will help reduce the risk of malware infection.
- Enable DoH: This is a protocol offered by most browsers that protects your DNS queries from spying and tampering. Some browsers, such as Chrome and Firefox, now offer it as default. Simply go into your browser’s settings, find “Security” or similar, and check “Use secure DNS” is toggled on.
Security measures for name servers and resolvers
Network and DNS administrators, as well as hosting providers, must enforce strict security practices, such as:
- Deploy DNSSEC: Domain Name System Security Extensions (DNSSEC) is a set of protocols that’s crucial for avoiding cache poisoning attacks and rogue DNS server attacks. Essentially, it’s a signature for DNS records that helps confirm the data hasn’t been altered. Cloudflare offers a great DNSSEC setup guide.
- Enforce strong access control: Limiting access to DNS settings can help minimize the attack area for malicious actors. In other words, only authorized admins should have login access to the DNS infrastructure. Multi-factor authentication (MFA) is an excellent tool for preventing unauthorized access.
- Monitor DNS logs: Monitoring DNS logs can help you spot unusual DNS query spikes, sudden requests to obscure domains, or repeated lookups for non-existent domains.
- Keep DNS software up-to-date: No matter which DNS service you use, it’s imperative to keep software up-to-date to patch the latest vulnerabilities.
- Eliminate redundant resolvers: A resolver is a server or software component responsible for querying DNS records. As such, unnecessary resolvers should be disabled. Also, resolvers should be placed behind a firewall, preventing access from outside the organization.
- Restrict access to name servers: Securing name servers (the servers that store the mappings of domain names to IP addresses) should involve physical and network security. Strong access control and physical security for server locations are imperative, as well as MFA and robust firewall rules.
- Protect against cache poisoning: Reduce the risk of cache poisoning by randomizing source ports, making it difficult for attackers to predict the port number. Also, mixing upper and lower case in domain names makes it harder for attackers to spoof DNS responses.
- Separate authoritative name servers from resolvers: If both services run on the same server, a distributed denial-of-service (DDoS) attack targeting one component could bring down the other. It’s recommended to separate the services onto different machines or infrastructure.
- Restrict zone transfers: Zone transfers allow secondary name servers (slaves) to request a copy of the DNS zone, containing vital information about your domain records. Limiting zone transfers helps reduce the chance of exploitation by criminals who are after critical DNS records.
Best practices for website owners
DNS hijacking can threaten your website’s credibility, customer loyalty, and traffic. Here’s how to lock down your domain and DNS settings:
- Limit DNS access to authorized users: Only a small, trusted group should be allowed to access deep-level settings. Two-factor authentication (2FA) adds an additional security layer to login processes.
- Enable client lock on domain registrars: Client lock (also known as domain lock or transfer lock) allows you to prevent unauthorized transfer or changes to your domain’s registration and DNS records. It protects against domain hijacking via social engineering or DNS record changes from third-party systems.
- Use a DNS registrar that supports DNSSEC: Top registrars like Cloudflare and Google Domains offer easy access to DNSSEC settings, making it possible to enable this feature without much fuss. Some registrars also support DoH and DoT, providing an extra shield to prevent DNS manipulation.
- Enforce HTTPS on your site: Implement a redirect rule on your server to automatically redirect any HTTP traffic to the HTTPS version of your site. This ensures visitors always access your site securely.
- Add an HSTS header: This header instructs browsers to only communicate with your site over HTTPS for a specified period. It's crucial for security, especially for sites handling sensitive data.
- Never self-sign certificates: Self-signed certificates lack trust validation and can lead to security risks. Browsers and other clients don't recognize self-signed certificates as legitimate and will display "not secure" warnings to users.
- Use Certificate Transparency monitoring: Certificate Transparency monitoring is crucial to ensure your Secure Sockets Layer (SSL) / Transport Layer Security (TLS) certificates are properly issued and to detect mis-issuances. By tracking certificates via public logs, you can identify unauthorized certificates, quickly address potential issues, and build trust in the certificate ecosystem.
- Enable certificate authority authorization (CAA): CAA enhances security by restricting which certificate authorities (CAs) can issue SSL/TLS certificates for your domain. This helps prevent unauthorized or malicious certificates from being issued.
DNS hijacking vs. DNS spoofing vs. cache poisoning
Terms like DNS hijacking, DNS spoofing, and cache poisoning are often used interchangeably. But while they’re closely related, they work differently. Let’s take a closer look.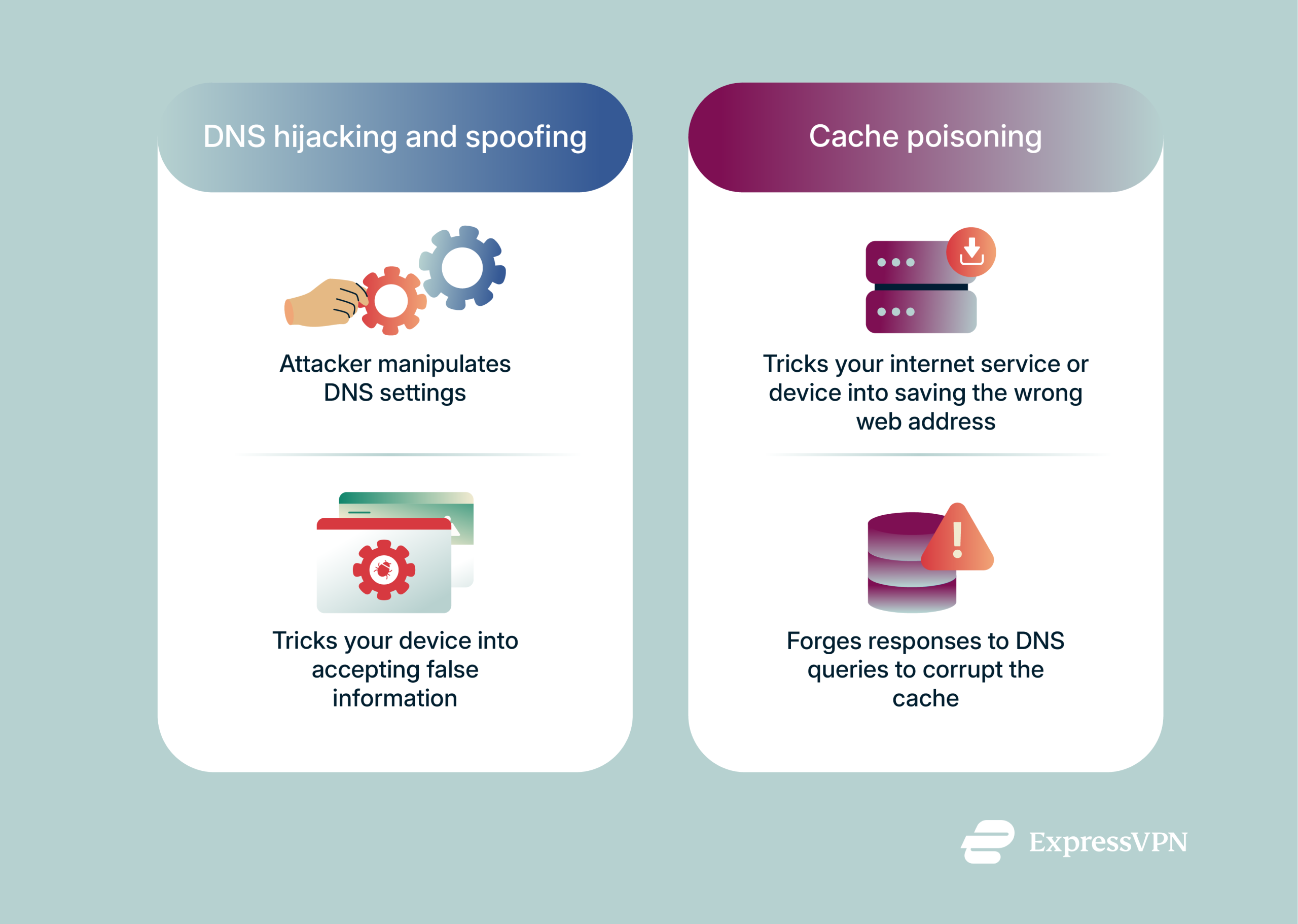
DNS hijacking and spoofing: How they work and who they target
DNS hijacking occurs when an attacker manipulates a user’s DNS settings, router DNS settings, website DNS server, or a domain’s registrar account to redirect the user to malicious domains. When the victim tries to access a legitimate site, they’re taken to a fake one instead.
DNS spoofing is a bit more subtle and involves forging DNS responses to trick a client or server into accepting a fake IP address. The result is the same, though: the victim is redirected to a fake site for phishing purposes or to serve malicious downloads.
Cache poisoning: How attackers corrupt DNS caches
Cache poisoning (also known as DNS cache poisoning or DNS poisoning) tricks your internet service or device into saving the wrong address for a website. Usually, the attacker will send a DNS query to a vulnerable DNS server for a specific domain.
While the resolver waits for a legitimate response, the attacker bombards it with forged responses, trying to force the forged response to arrive before the legitimate one. At that point, the resolver caches it, and its cache becomes corrupted.
In other words, cache poisoning attacks force DNS servers to store fake information and send users to fake websites.
DNS hijacking vs. redirection attacks
DNS hijacking and redirection attacks are fundamentally different. While DNS hijacking happens before you reach the intended website, redirection attacks occur after a connection to a website or server has already been established.
Furthermore, redirection attacks happen on compromised sites and web apps within the victim’s browser (via malicious JavaScript or injected code) or through misconfigured web servers, as opposed to DNS hijacking that happens on a user’s device (on the operating system level) or on a DNS server.
| Feature | DNS hijacking | Redirection attacks |
| Where it occurs | DNS layer | Application layer |
| Timing | Before a site is loaded | After a site is loaded |
| Visibility | Most often invisible | Detected by browser tools |
| Defenses | VPN, DNSSEC, DoH, DoT | Web app firewall, secure coding, content security policies |
The global impact of DNS hijacking
DNS hijacking is widespread and affects millions of users and organizations. It’s also used for censorship, financial fraud, and more.
How widespread is DNS hijacking?
DNS hijacking incidents range from regional ISP-level manipulation to full-scale espionage campaigns targeting entire industry sections. Here are some of the most talked-about incidents.
- Curve Finance attack (2022): In this DNS attack, visitors to Curve Finance’s websites were redirected to a malicious domain connected to the attacker’s digital wallet. During this attack, the perpetrators obtained a total of $573,000 in assets via Ethereum.
- Sea Turtle campaign (2017-2019): This malicious campaign used rogue DNS servers and stolen credentials to hijack traffic from 10+ organizations across the Middle East, North Africa, and Europe. It focused on telecom providers, government agencies, and energy firms.
- DNSpionage attacks (2018): In this attack, malicious actors targeted Lebanese and UAE government domains through cache poisoning. Cybersecurity experts believe that malicious Word documents were used as an entry point, ultimately leading to a DNS server compromise.
- Brazilian banking DNS hijacks (2011-2016): In this malicious campaign, cybercriminals used mass-scale router DNS hijacks to redirect users to fake banking portals. Attackers managed to change DNS settings on millions of consumer routers in Brazil, hugely impacting the domestic banking sector.
FAQ: Common questions about DNS hijacking
Is DNS hijacking common?
Cybercriminals often use it to redirect users to fake websites for phishing, ads, or malware distribution. It’s particularly effective because users typically don’t notice anything is wrong; the web address looks correct, but they’re not actually on the intended site.
DNS hijacking is also used by some governments or internet service providers (ISPs) for censorship or traffic redirection. Because it can occur at both the local and network levels, it remains a widespread threat.
Does a VPN prevent DNS hijacking?
A quality VPN like ExpressVPN uses private DNS servers with end-to-end encryption, making hijacking extremely difficult.
Additionally, ExpressVPN comes with Advanced Protection tools, which help reduce the chances of visiting malicious sites, being tracked by advanced trackers, or seeing sketchy ads.
What can cybercriminals do with my DNS?
How to change my DNS servers for better security?
You can also check if your browser has DNS over HTTPS (DoH) enabled. To do this, go to your settings, find “Security” or similar, and look for the “Use secure DNS” option.
What’s the difference between DNS poisoning and DNS hijacking?
DNS poisoning, also known as DNS cache poisoning, involves corrupting the DNS cache of a resolver by injecting false DNS records, causing users to be redirected to malicious sites without altering the resolver’s settings.
How can I tell if my ISP is hijacking my DNS?
Also, DNS redirection on the ISP level can trigger certificate errors for websites you normally trust. For example, if you start seeing an error that says “this site can’t provide a secure connection” on a site you’ve visited many times before, that could be a sign of DNS hijacking by your ISP.
What causes DNS hijacking?
How can businesses protect their DNS infrastructure?
Can DNS hijacking be used for phishing attacks?
Is public Wi-Fi more vulnerable to DNS hijacking?
How do I know if my DNS is secure?
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN