What is URL phishing? Everything you need to know

Every day, countless people click on links while browsing the net or reading their emails. Many are perfectly safe and send the user to trusted, legitimate websites.
However, some links are malicious traps, redirecting users to fake, dangerous sites that can steal their personal data. This is known as URL phishing: a common scam technique employed by cybercriminals across the globe.
This guide looks at what URL phishing is, how it works, and how to avoid it.
Understanding URL phishing
In a nutshell, URL phishing is a scam technique that involves cybercriminals tricking people into clicking links and visiting fraudulent websites.
Often, they’ll design the links to appear legitimate and enticing, deploying them over email, SMS, or other messaging platforms. The links also often direct to sites that appear safe and genuine, with many made to look just like well-known social media platforms, online marketplaces, bank websites, and so on.
In reality, these sites are typically fake and malicious in nature, manned by cybercriminals who lie in wait for victims to click the links and end up on their sites. Once there, the victims are often lulled into a false sense of security and may inadvertently give away their data. They might hand over their usernames and passwords, for example, thinking that they’re logging into a safe site.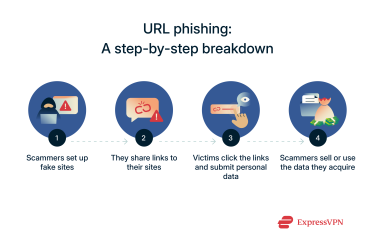 The reason this scam works so well is largely due to the fact that the scammers use a range of tools and techniques to make you feel that the links and sites are safe. Even for experienced internet users, it can sometimes be hard to tell a malicious link or URL apart from a real one. Because of this, hundreds of thousands of people fall victim to URL phishing each year.
The reason this scam works so well is largely due to the fact that the scammers use a range of tools and techniques to make you feel that the links and sites are safe. Even for experienced internet users, it can sometimes be hard to tell a malicious link or URL apart from a real one. Because of this, hundreds of thousands of people fall victim to URL phishing each year.
Types of URL phishing attacks
All URL phishing attacks revolve around scammers encouraging victims to click links, but the exact nature of these attacks can vary. Here are some of the various types of URL phishing tactics that scammers use:
Typosquatting
This attack involves scammers setting up fake websites with URLs that are very similar to existing, legitimate sites, but with a slight spelling change. They then hope that users might accidentally make a typo when entering the URL and end up on their fake sites, which are made to look just like the real ones. An example could be “Googel” instead of “Google.”
Masked links
This technique involves hiding a malicious link behind one that appears perfectly safe. The scammers might write out the URL of a website you know and trust so you think that’s where the link is taking you. In reality, it takes you to a completely different site, and you can only see the real link if you hover your cursor over it or inspect it.
Legitimate but compromised domains
In some cases, scammers and cybercriminals are able to obtain access to genuinely legitimate websites, compromising their security. They can then simply sit and wait for users to log on and hand over their data through user forms or download malicious files. Since the site appears safe and real, users are even more likely to fall victim to this type of attack.
Malformed prefixes
Many users skim URLs quickly and may not notice small differences in the prefix, especially if the rest of the domain looks correct. Attackers exploit this by making the URL look legitimate at first glance, for example, by substituting a W with two Vs in wvvw.google.com.
Subfolder tricks
These attacks involve real domains that have been compromised. The scammers gain access to a legitimate domain somehow and create a new malicious subfolder or webpage, like “legitsite.com/maliciouspage.” The user assumes that this page is safe since it’s tied to a legitimate website. But it’s actually controlled by scammers.
Redirect chains
Some websites use redirects to automatically send users to different websites or pages. Scammers can use that technique to their advantage. They create a link that looks like it’ll send you to a safe, legitimate website but set it up to redirect you to one of their fake, malicious sites instead.
HTTPS and SSL spoofing
This form of URL phishing involves attackers creating sites that are absolutely identical to legitimate ones in almost every possible way. The big difference is that instead of having secure HTTPS connections and Secure Sockets Layer (SSL) certificates, they’re actually unsafe, malicious sites used to steal people’s data.
Image-based URL phishing
Most links are text-based, but it’s also possible to hide links in images or other page elements, too. Attackers can therefore conceal their malicious URL phishing links behind pictures, banners, or even inside QR codes, so when users click or scan what seems to be an innocent image or code, they end up on a harmful site. This technique completely eliminates the need to disguise the URL into something legitimate-looking since it remains invisible all the time.
Mixing malicious with legitimate links
This attack involves scammers sending emails and messages or creating entire web pages with a mixture of links embedded into them. Some of those links are safe and legitimate, sending you to real sites. Others, however, are malicious, but the presence of some safe links lulls victims into a false sense of security.
How to identify a phishing URL
Knowing how to spot a phishing link or fake URL is important if you want to avoid becoming one of the many victims of this sort of scam. Here are some ways to spot phishing links:
Spotting subtle misspellings
Before clicking a link, read the URL carefully. As explained earlier, phishing links often look very similar to legitimate ones, but with slight differences and telltale signs, like typos, extra characters, or different domain names, like .net at the end instead of .com.
Hovering over links for previews
On desktop devices and laptops, you can hover your cursor over a link to see where it’s going to send you. The address will usually appear in the bottom corner of your web browser window. If you’re suspicious and wondering, “Is this a phishing link?” then always hover over it to check.
Verifying HTTPS and domain certificates
Legitimate sites have “HTTPS” at the start of their URL addresses, which is a sign that the site is secure and has an SSL certificate. Fake sites may still have HTTPS addresses, but more often than not, they tend to just have “HTTP” at the start.
Using browser security indicators
Many browsers have built-in security tools that alert you if you’re being sent to a suspicious or malicious website. All reputable antiviruses offer phishing protection as well, commonly in the form of browser extensions. Use these security tools and indicators to avoid ending up on unsafe sites.
Cross-checking with URL and malicious QR code scanners
URL scanners are tools that can check website links for you, letting you know about possible threats, like malware or suspected phishing links. If you want to check a link for phishing, it’s worth bookmarking and using a URL scanner to do so. Similarly, to check a QR code without visiting the site it leads to, use a QR code scanner that lets you preview the link before opening it.
Real-world URL phishing examples
 Next, let’s explore how URL phishing attacks tend to actually appear, with a look at some of the most common ways scammers dress up their links to fool their victims.
Next, let’s explore how URL phishing attacks tend to actually appear, with a look at some of the most common ways scammers dress up their links to fool their victims.
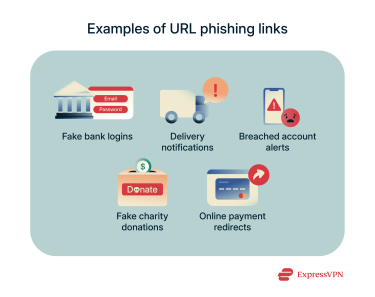
Fake bank login page
Scammers often create fake bank account emails, alerts, and login pages, scaring victims into thinking they owe money or that their finances are at risk. Panicked, victims are more likely to click links and type in their details, handing over account access to the criminals.
Delivery notification scam
With more and more people shopping online, scammers are increasingly creating fake delivery notifications for services like FedEx or USPS. The messages usually ask you to confirm your details before you can receive a package but actually take you to fake sites.
Breached account alert
Many URL phishing messages conceal links in messages that are designed to frighten or panic the victim. Some messages might say that one of your online accounts has been hacked, for example, and you need to click a link and confirm your details to recover the account.
Fake charity donation link
A particularly cruel method that some scammers employ is to send messages pretending to be from charities and non-profit organizations, asking users to donate to worthy causes. In reality, victims are just giving money straight to scammers.
Online shop payment redirect
This scam technique involves scammers creating fake sites that resemble real online marketplaces and stores. They send you a promotional message, usually via email, with links inside sending you to their fake site, where you might give away your payment details.
How to report a phishing URL
Billions of phishing emails are sent daily, so it’s highly likely you’ll encounter phishing links from time to time. If so, there are steps you can take to report them and play your part in stopping the scammers.
Contact the impersonated organization
If a fake URL is pretending to be a link for a trusted site like a bank, store, or social media platform, you can contact the real company and let them know.
Report via browser tools
Various browser tools exist to make it quick and easy to report suspected scams, like Safe Browsing on Google Chrome.
Submit to security vendors
You can also let security specialists like antivirus developers or vendors know about suspected phishing websites so they can take appropriate actions to stop them.
Inform your email/chat provider
If you’re getting phishing links delivered to your email inbox or via DMs on a chat platform, it’s worthwhile to inform the platform’s support team, as they may be able to identify and block the offending accounts.
Notify cybersecurity agencies (e.g., FTC, CISA)
You can also report all sorts of online scams and malicious activities to leading authorities, like the Federal Trade Commission (FTC), Cybersecurity and Infrastructure Security Agency (CISA), or the National Cyber Security Centre in the U.K.
Protect yourself from URL phishing with ExpressVPN Threat Manager
Knowing how to spot URL spoofing and phishing links is one big step toward staying safe. But a much easier method is to let dedicated protection tools do this for you automatically.
One such tool is ExpressVPN’s Threat Manager, which comes with every ExpressVPN subscription. It automatically identifies and blocks threats you might encounter during online sessions. It can spot phishing links, malicious sites, malware, and spam-spreading domains without you having to lift a finger.
Threat Manager does this by comparing website URLs with a continuously updated, curated list of known fraudulent or harmful websites and blocking any connection before danger can reach you.
FAQ: Common questions about URL phishing answered
What happens if I click on a phishing link?
You may not be at risk right away, but if you enter any personal information on the fake site you visit or click other links, you could end up giving away personal data, downloading viruses, or being scammed in other ways.
What can phishing links do?
Phishing links can fool users into visiting sites that appear genuine, tricking them into giving away their data, paying for products that don’t exist or won’t be delivered, or downloading malware.
How do I remove a URL phishing attack?
You can delete any suspected phishing messages sent to you and report suspected phishing sites to various authorities so that they can take steps to have them removed.
What is an example of URL phishing?
An example might be a scammer creating a fake site that looks just like your online bank. They then send you a message, claiming that there’s an issue with your account and asking you to click a link and confirm your details. If you click and enter your credentials on the fake site, you could give away that information to the scammers.
What does a suspicious URL look like?
Suspicious or phishing URLs may seem perfectly safe and legitimate at first glance but often have typos or other subtle differences that separate them from genuine, trusted web addresses.
What is an example of URL spoofing?
An example of URL spoofing would be something like “amaz0n.com” or “amazon1.com,” which are both designed to look like official Amazon links but with slight differences.
How do I know if a URL is phishing?
You can read it to look for any typos or inconsistencies, hover your mouse over it to see where it wants to send you, or use tools like URL scanners or ExpressVPN’s Threat Manager, included with our VPN subscription, to help you spot and block phishing sites automatically.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN